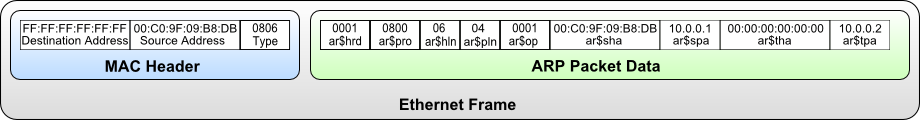
The ARP Scan Tool (AKA ARP Sweep or MAC Scanner) is a very fast ARP packet scanner that shows every active IPv4 device on your subnet. Since ARP is non-routable, this type of scanner only works on the local LAN (local subnet or network segment).
The ARP Scan Tool shows all active devices even if they have firewalls. Devices cannot hide from ARP packets like they can hide from Ping.
- Send ARP packets to any number of destination hosts, using a configurable output bandwidth or packet rate.
This is useful for system discovery, where you may need to scan large address spaces. - Construct the outgoing ARP packet in a flexible way.
arp-scan gives control of all of the fields in the ARP packet and the fields in the Ethernet frame header. - Decode and display any returned packets.
arp-scan will decode and display any received ARP packets and lookup the vendor using the MAC address. - Fingerprint IP hosts using the arp-fingerprint tool.
How to install arp-scan
To install arp-scan on Ubuntu or Debian:
# sudo apt-get install arp-scan
To install arp-scan on CentOS, Fedora or Redhat:
# sudo yum install arp-scan
To detect IP address with arp-scan, run the following.
# sudo arp-scan -I eth1 -l Starting arp-scan 1.9.2 with 32 hosts (http://www.nta-monitor.com/tools-resources/security-tools/arp-scan/) 10.10.11.193 cc:4e:24:c7:71:14 test Communications Systems, Inc. 10.10.11.194 00:50:56:3e:57:25 VMware, Inc. 10.10.11.196 00:50:56:09:67:4e VMware, Inc. 10.10.11.197 00:50:56:w4:1d:fb VMware, Inc. 10.10.11.199 00:50:56:61:f8:f6 VMware, Inc. 10.10.11.202 00:50:56:a2:0d:09 VMware, Inc. 10.10.11.203 00:50:56:89:2n:a8 VMware, Inc. 10.10.11.204 00:50:56:89:27:77 VMware, Inc. 10.10.11.205 00:50:56:59:76:e7 VMware, Inc. 10.10.11.206 00:50:56:2e:3a:e3 VMware, Inc. 10.10.11.207 00:50:56:89:18:33 VMware, Inc. 10.10.11.208 00:50:56:2e:21:60 VMware, Inc. 10.10.11.209 00:50:56:1e:27:0a VMware, Inc. 10.10.11.210 00:50:56:89:24:46 VMware, Inc. 10.10.11.211 00:50:56:1e:3b:9a VMware, Inc. 10.10.11.212 00:50:56:89:3c:11 VMware, Inc. 10.10.11.216 00:50:56:2e:1e:da VMware, Inc. 10.10.11.218 00:50:56:3e:21:5c VMware, Inc. 10.10.11.220 00:0c:29:57:69:74 VMware, Inc. 10.10.11.222 00:50:56:8e:31:66 VMware, Inc. 10.10.11.213 00:50:56:89:45:00 VMware, Inc. 10.10.11.214 00:50:56:89:44:d8 VMware, Inc. 10.10.11.215 00:50:56:c4:1d:bb VMware, Inc. 10.10.11.217 00:50:56:89:3a:0f VMware, Inc. 10.10.11.219 00:50:56:49:12:db VMware, Inc. 10.10.11.221 00:50:56:89:8c:a6 VMware, Inc.
That’s it.
How to detect IP address conflicts
If you have any IP address conflict issue, you can see any two different MAC addresses are claiming the same IP address.