The Docker Registry Manager Web front End for managing multiple private docker registries. It is a golang written, beego driven, a web interface for interacting with multiple docker registries. This project is to provide the user interface for your private Docker registry v2 and manage more than one docker private registry server.
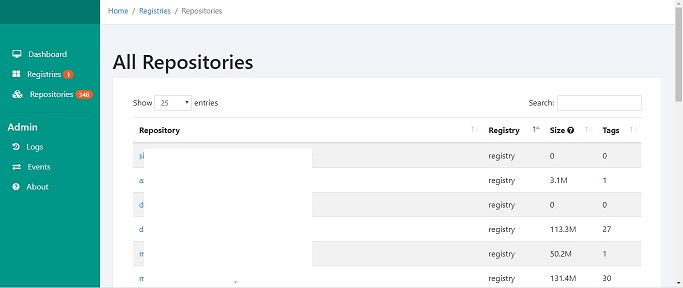
This containerized web application that provides administration of one-to-many private registries with features like manage registry repository, delete and activity logs.
Features
- Support for docker distribution registry v2 (https and http)
- Viewable image/tags stages, commands, and sizes.
- Bulk deletes of tags
- Registry activity logs
- Comparison of registry images to public Docker hub images
Install Docker Registry Manager
You have a docker registry currently running and contain many images. The steps to install it through the Docker-Compose.
# git clone https://github.com/snagles/docker-registry-manager.git && cd docker-registry-manager
# vim registries.yml # add your registry
Registries.yml Example
registries:
Registry:
url: http://localhost # Example https://localhost, http://remotehost.com
port: 5000 # Example: 443, 8080, 5000
username: exampleUser
password: examplePassword
refresh-rate: “5m” # Example: 60s, 5m, 1h
skip-tls-validation: true # REQUIRED for self signed certificates
dockerhub-integration: true # Optional – compares to dockerhub to determine if image up to date
# vim docker-compose.yml # Edit application settings e.g log level, port
Environment Options:
MANAGER_PORT: Port to run on inside the docker container
MANAGER_REGISTRIES: Registries.yml file location inside the docker container
MANAGER_LOG_LEVEL: Log level for logs (fatal, panic, error, warn, info, debug)
MANAGER_ENABLE_HTTPS: true/false for using HTTPS.
MANAGER_KEY: key file location inside the docker container
MANAGER_CERTIFICATE: Certificate location inside the docker container
# sudo curl -L https://github.com/docker/compose/releases/download/1.22.0/docker-compose-$(uname -s)-$(uname -m) -o /usr/local/bin/docker-compose # sudo chmod +x /usr/local/bin/docker-compose
# docker-compose up -d
Now you can connect it <host>:8080
Docker Registry Manager Planned Features
- Authentication for users with admin/read only rights using TLS
- Global search
- List image shared layers
- Event timeline