Darkstat a stable and fast network monitoring tool which helps the network administrators to monitor their router/firewall and server bandwidth and traffic. The biggest advantage of using this tool is that we can get per host/ip traffic stats which will be very helpful for the administrators to analysis the problem. If includes the following features.
- In-build web-server which can run on any TCP ports.
- Enabled deflate compression on the web server.
- Traffic graphs, reports per host, shows ports for each host.
- RDNS look-ups using a child process.
- Portable and single threaded.
- Very easy to install and configure.
Installing Darkstat
Installation can be done either via rpm or source. Before installing the tool make sure that you have installed the libcap package (yum install libcap).
Darkstat rpm available at : http://packages.sw.be/darkstat/
Download Darkstat source from : http://dmr.ath.cx/net/darkstat/darkstat-3.0.713.tar.bz2
- # cd /usr/src
- # wget http://dmr.ath.cx/net/darkstat/darkstat-3.0.713.tar.bz2
- # bunzip2 darkstat-3.0.713.tar.bz2
- # tar xvf darkstat-3.0.713.tar
- # cd darkstat-3.0.713
- # ./configure && make && make install
It should go fine without any errors. I have tested in my latest CentoS 5.x /RHEL 6 and Fedora and all went fine without any errors.
Starting the Darkstat web server
Since it is having a tiny web server with dflate compression enabled, just execute the following command to start the web server on
the specific server. For example if you like to run it it on port 81 to monitor the eth0 interface and also make sure that port 81 is open in your firewall.
- # darkstat -p 81 -i eth0
Use the lsof -i tcp:81 and make sure the web-server is running on port 81.
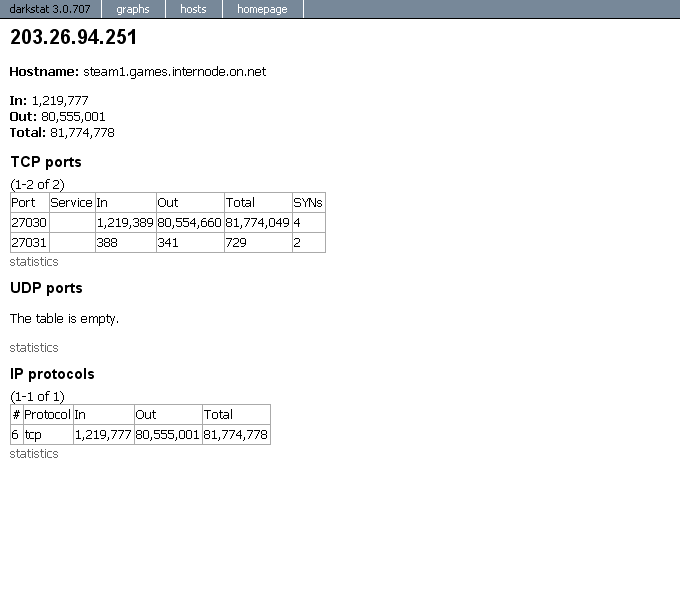
Open your web browser and type http://<serverIP or Hostname>:81 to open the web interfaces like in the below screen-caps.
In order to bind a certain port to a specific interface, you can use the option “-b”. In the following example to the local loopback address:
- # darkstat -b 127.0.0.1 (or) <yournewIP>
Persistent DNS-Resolution can be prevented by the parameter “-n”. This may be good for people without a flatrate or a dedicated line.
- # darkstat -n
Use option “-P” to prevent “darkstat” from putting the interface into “promiscuous mode”.
- # darkstat -P
With parameter “-e” you can perform a packet filter expression.
- # darkstat -e “port not 22”
Parameter “-d” you can specify the directory where “darkstat” creates its database.
- # darkstat -d /directory
Option “-v” activates the “verbose mode”:
- darkstat -v
Useful Links :
Darkstat Home Page
Darkstat Man Page
Screen-Caps :